Distinguishing e-signatures from e-seals
In eIDAS regulation, e-signatures and e-seals address different issues.
E-signatures engage the individual responsibility of the signatory.
E-seals are designed to give technical guarantees about the integrity and origin of the sealed data.
Display in Woleet.ID Server administration interface
In Woleet.ID Server, you manage identities linked to cryptographic keys.
When identities refer to physical persons, we call them user identities, and you manage them in a dedicated page.
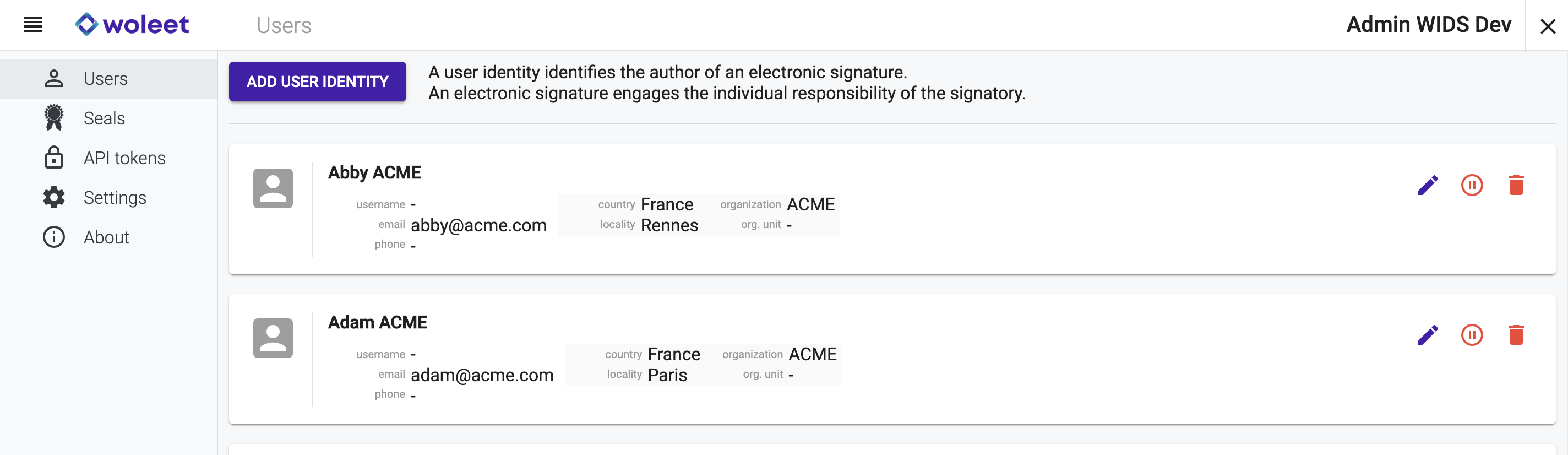
When identities refer to legal persons or technical entities, we call them seal identities, and you manage them in a dedicated page.
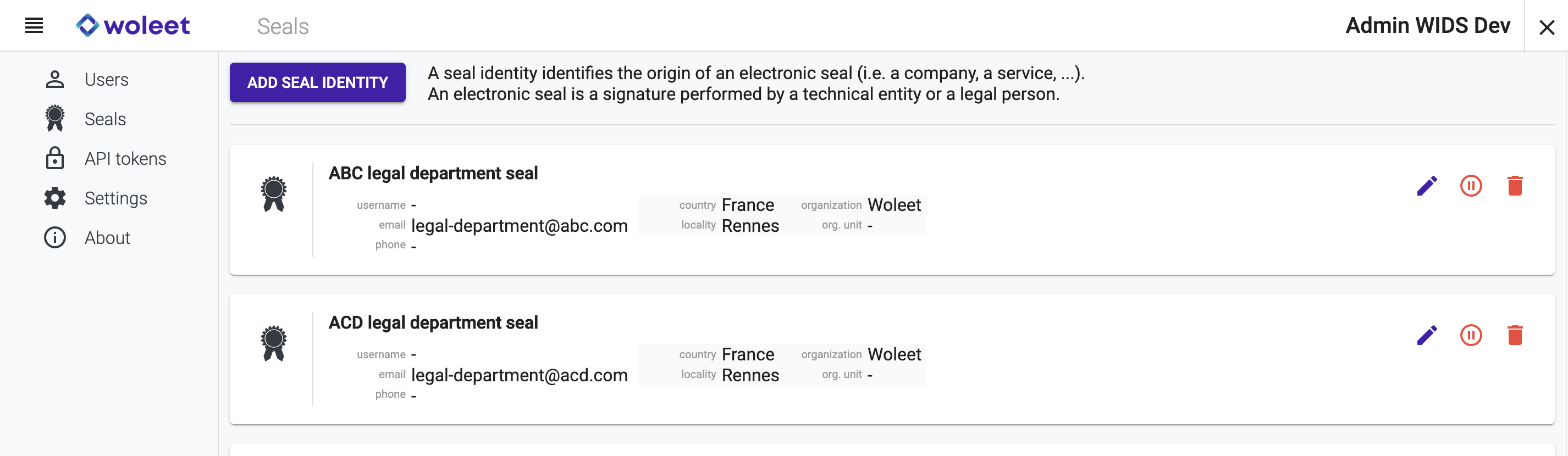
Identity attributes and authentication profile
A user identity and a seal identity can be described by following attributes:
- Common Name
- Organization
- Organization Unit
- Locality
- Country
- UserId
Furthermore, we use an email attribute as a unicity criteria within the identity database. You cannot create two identities with the same email (either being a user or a seal identity). It is possible to create a seal identity without an email. You will be warned if you are about to create a double entry.
For user identities, the email is part of an authentication profile that serves within the signature process. In the authentication profile, you also have a password, and you may also have a phone number. Before signing, the user shall authenticate with his/her password, or via an API token, and optionally via an OTP code received by SMS.
For seal identities, the email is mainly used to send notifications to a point of contact, a person who will be in charge of managing the seal keys, notably in case of name change, key expiration or key revocation. If the email is defined for the seal identity, an authentication profile (with a password) is created. Before creating a seal, the caller shall authenticate via the password or an API token.
It is not possible to transform a user identity into a seal identity and reciprocally, as the uses and stakes are too different.
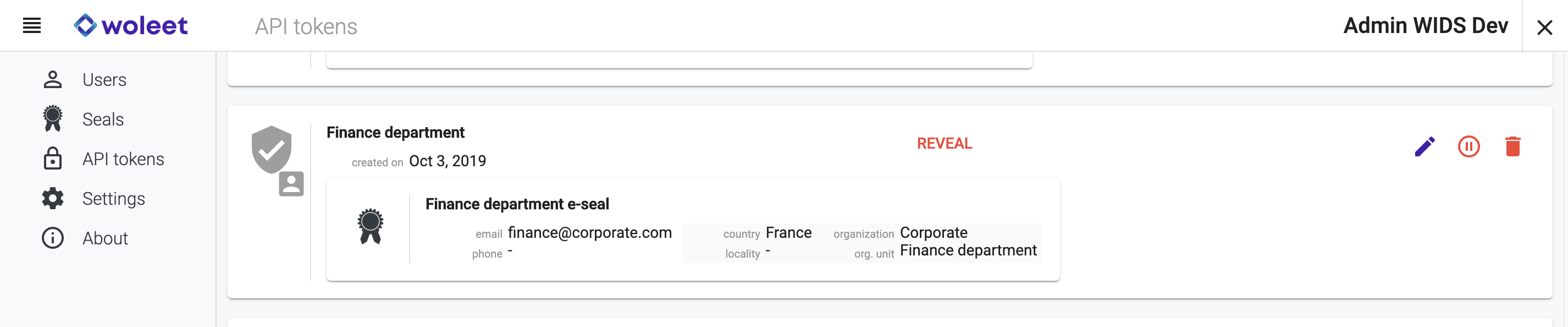
Protecting user or seal keys via an API token
API tokens are authentication means protecting the use of user or seal keys.
It is possible to create API tokens dedicated either to a given user identity, or to a seal identity.
Compatibility with Woleet signature and enrolment functions
Signature requests in ProofDesk can involve either user or seal identities, provided they have an email defined.
Signatures made via ProofKeeper can involve either user or seal identities, provided they are protected by an API token.
The key enrolment function allows a user to register in Woleet.ID Server a key that he/she holds on a personal device (mobile, Ledger): see documentation here.
This function is restricted to user identities (seal identities are not concerned).
Verifying organization existence and key possession (for seal identities only)
A seal identifies an organization. At time of validation, Woleet allows you via an "Identity URL" to verify that this organization is still there, and is still in possession of the seal key.
This identity URL is present in the signature proof receipts. Connecting to this identity URL allows you to check the identity information about the seal. Besides:
- This identity URL is protected by a TLS certificate that proves the existence of the organization.
- When connecting to the identity URL, a key proof-of-possession mechanism is implemented. It relies on a standard challenge/response cryptographic protocol. This proves the possession of the seal key.
Updated about 6 years ago
